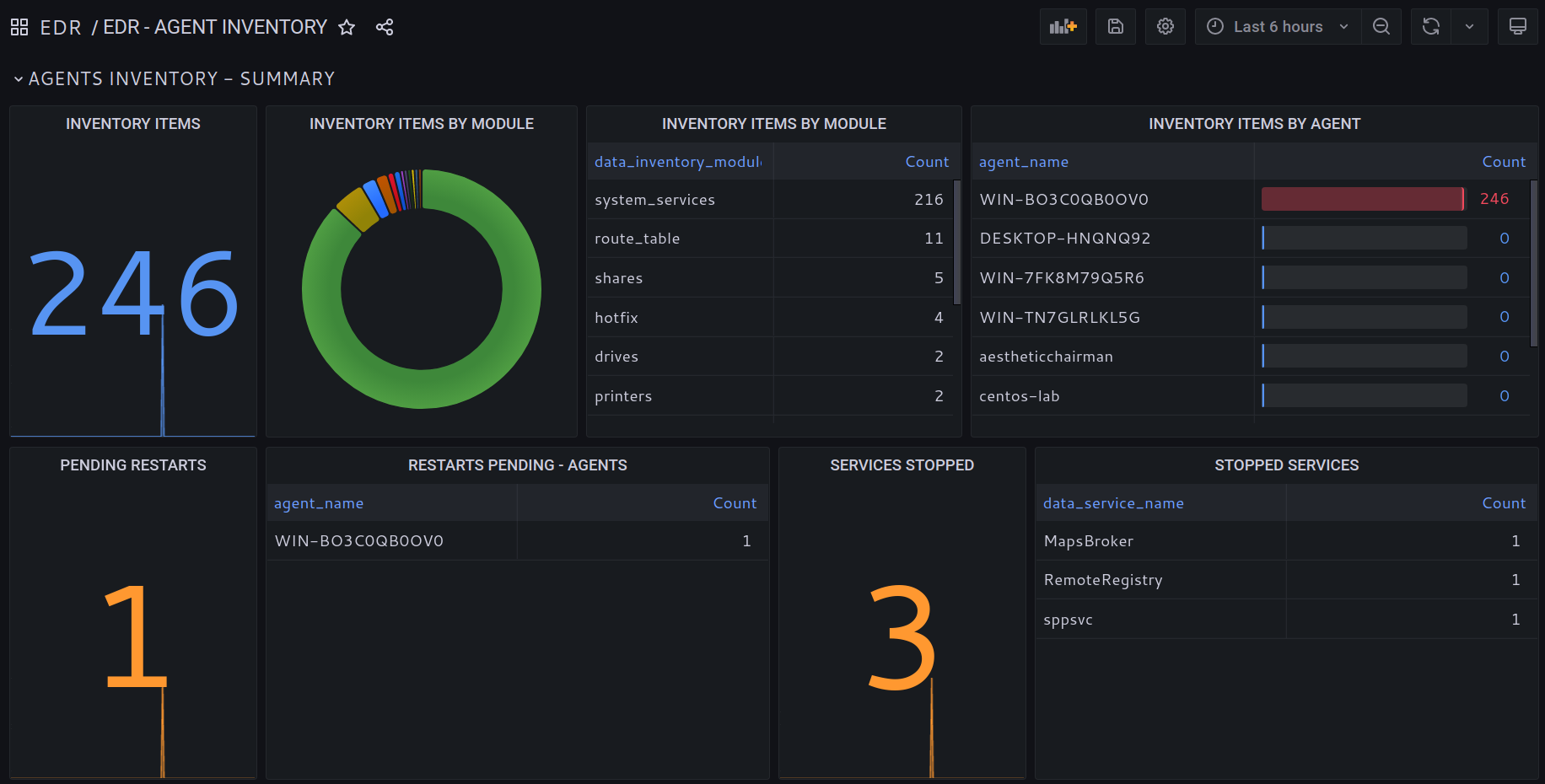
Software Vulnerabilities
Keep all your systems and software up to date and avoid exploitation of well-known vulnerabilities.Windows Defender and Advanced Security.
SOCFortress EDR collects and analyzes Windows Defender and Advanced Security events.Persistent footholds.
Find out if previous, successful intrusions in your environment left malware or undesired code that'll persist system reboots.Malicious Executables and DLLs.
Spot malware or undesired code still present in Users folders.EDR CapabilitiesPREVENTION.
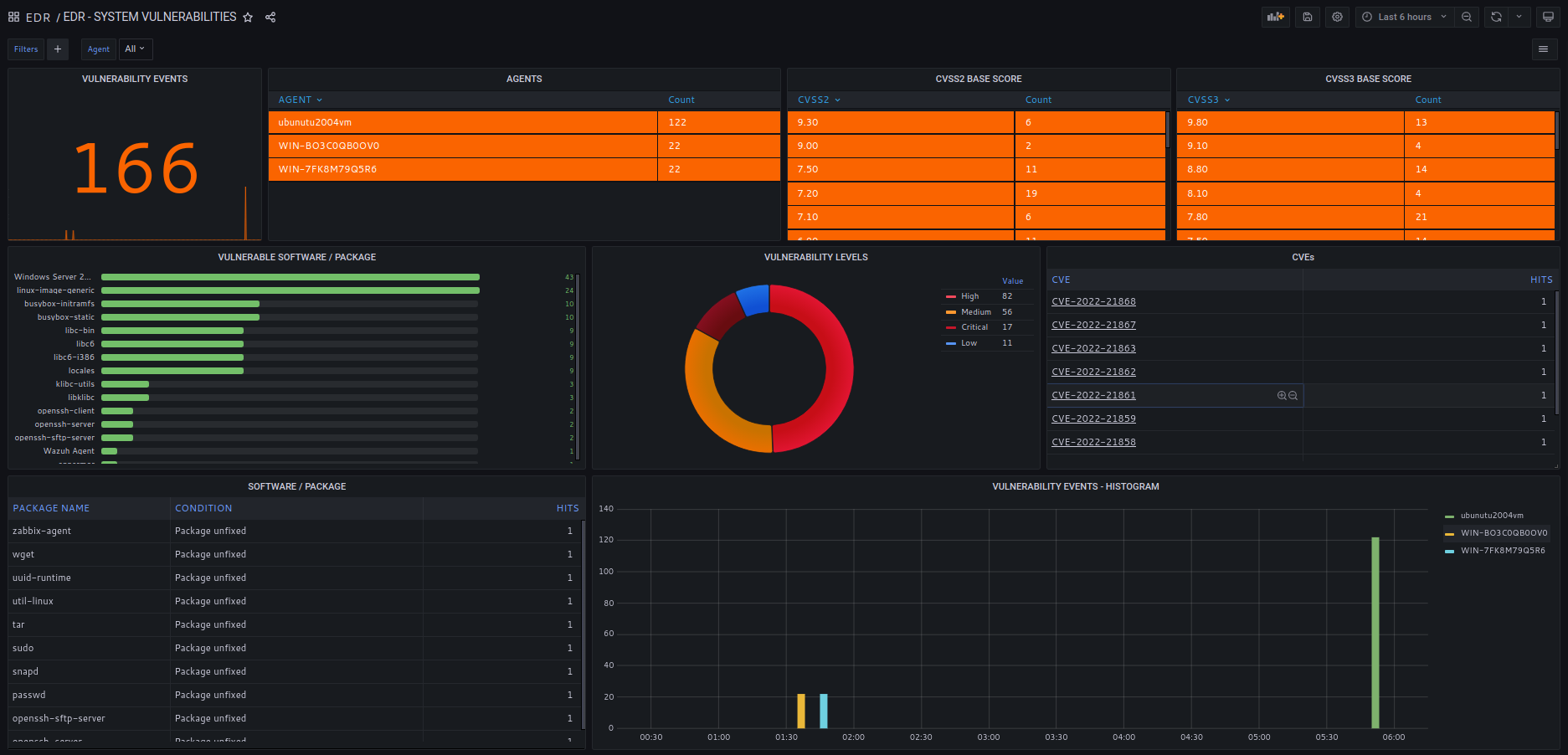
SOCFortress EDR agent inludes a vulnerability scan process, aligned with NIST vulnerability database to find Operating System and Installed software vulnerabilities. CVEs codes, description and scores included.
Keep all your systems and software up to date and avoid exploitation of well-known vulnerabilities.
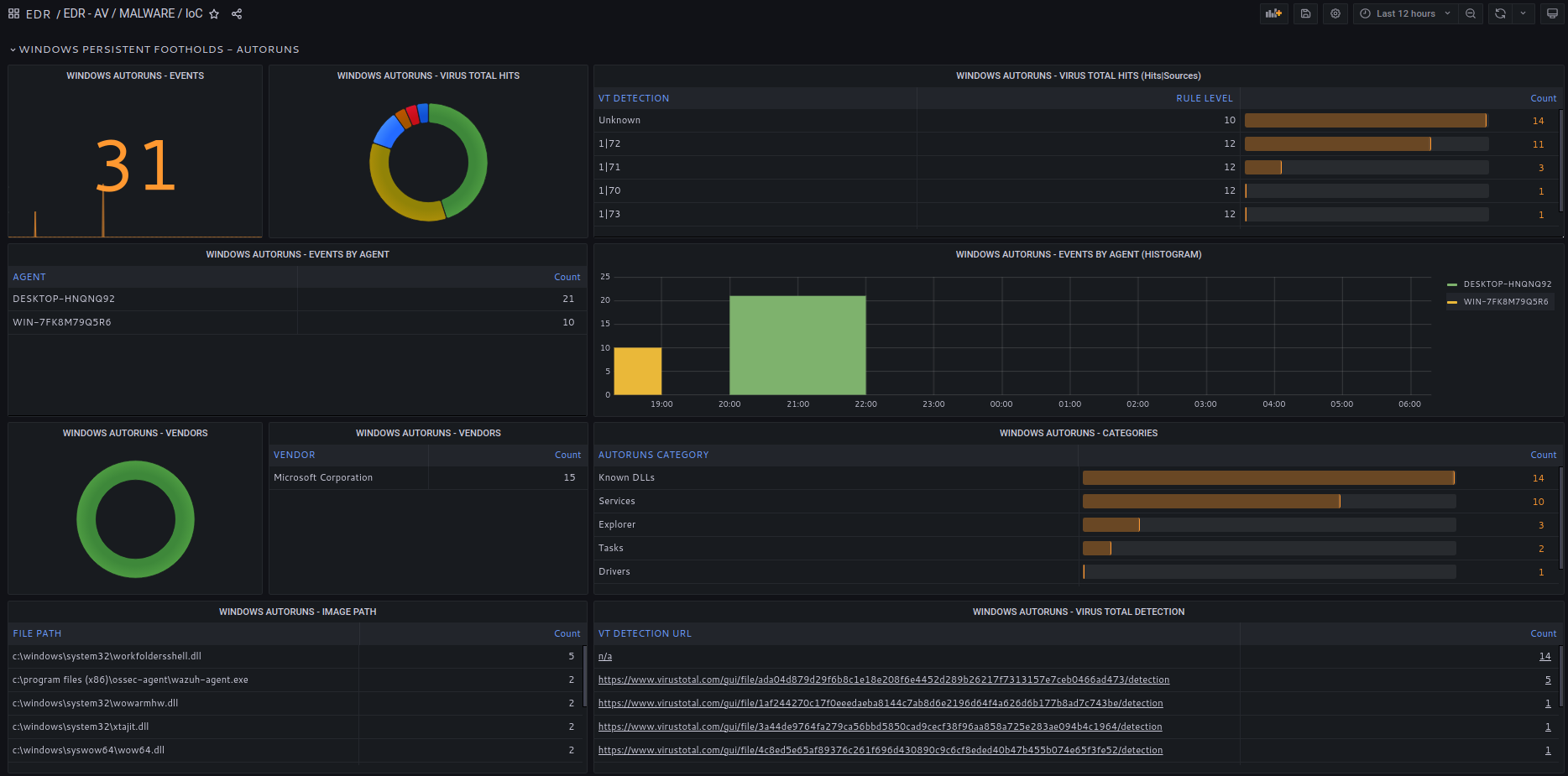
SOCFortress EDR agent analyzes the Windows Registry and runs all keys loaded at boot time against Virus Total.
Find out if previous, successful intrusions in your environment left malware or undesired code that'll persist system reboots.
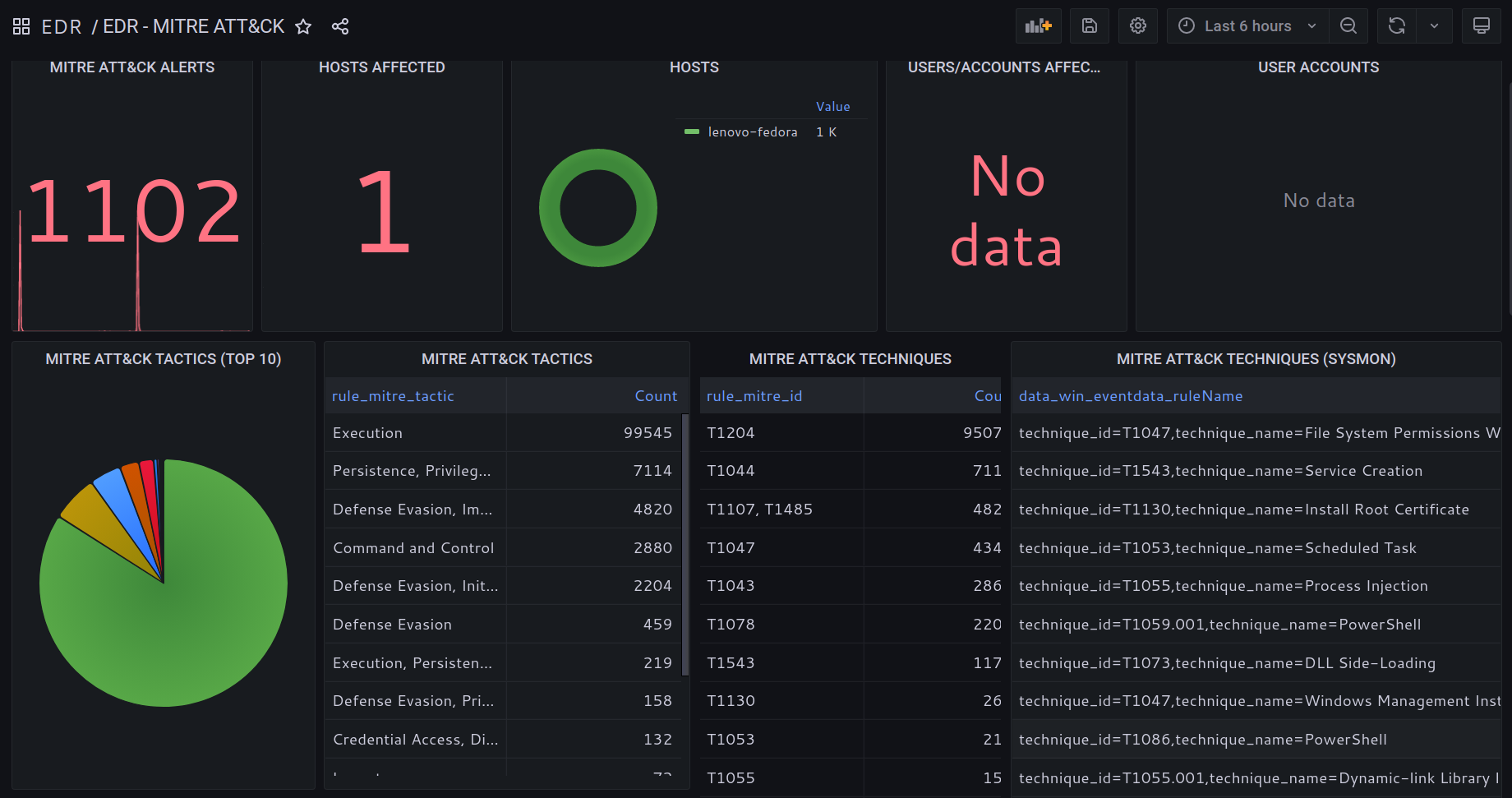
SOCFortress EDR agent analyzes system settings in Windows and Linux based Operating Systems.
Implement a sound systems hardening policy aligned with the Center for Internet Security benchmarks.
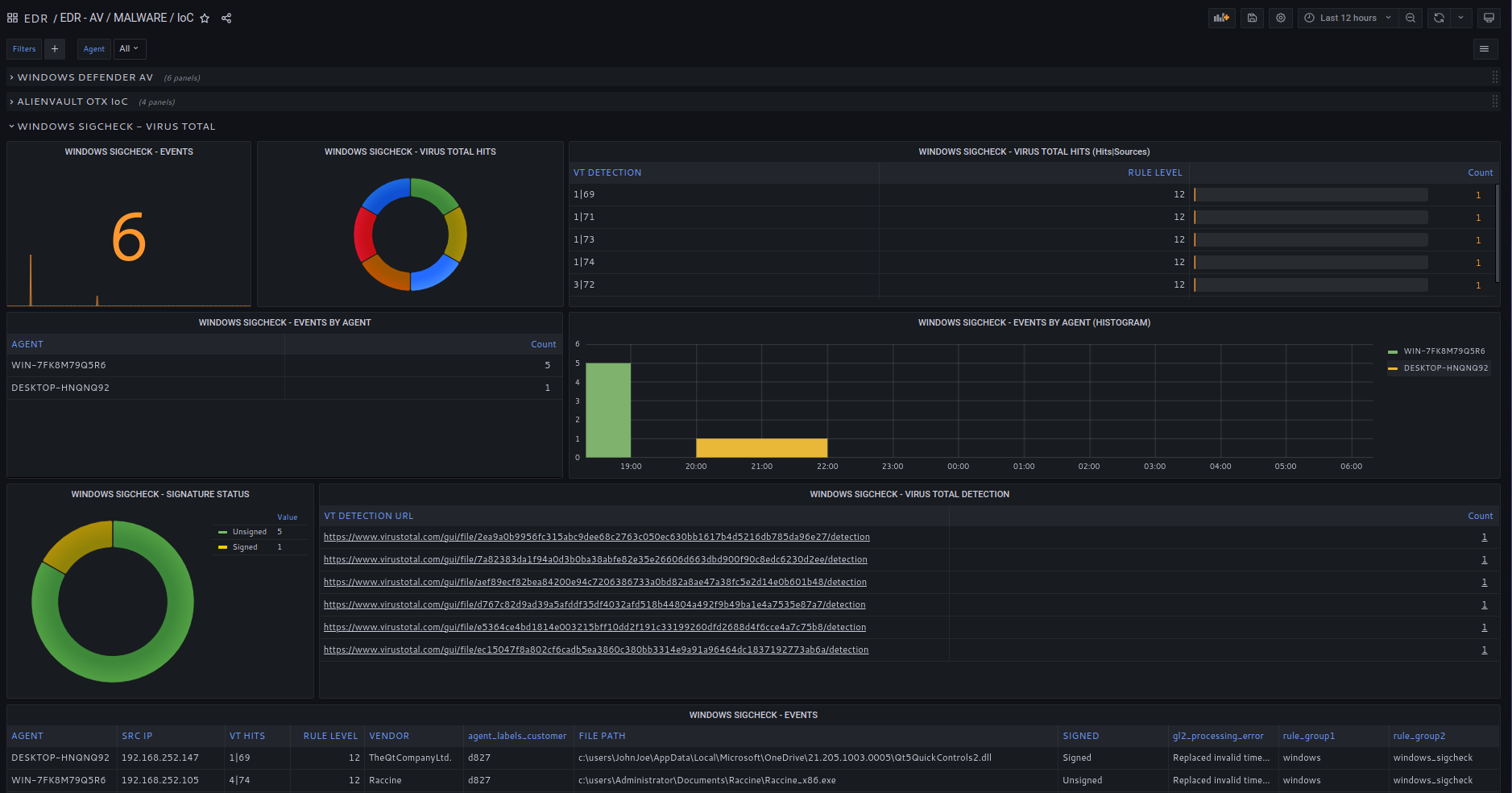
SOCFortress EDR will go through executables and DLLs found in the Users folders and will check all files signatures against Virus Total.
Find out if previous, successful intrusions in your environment left malware or undesired code still present in Users folders.
File-hash scan and analysis is the bread and butter in any EDR solution.
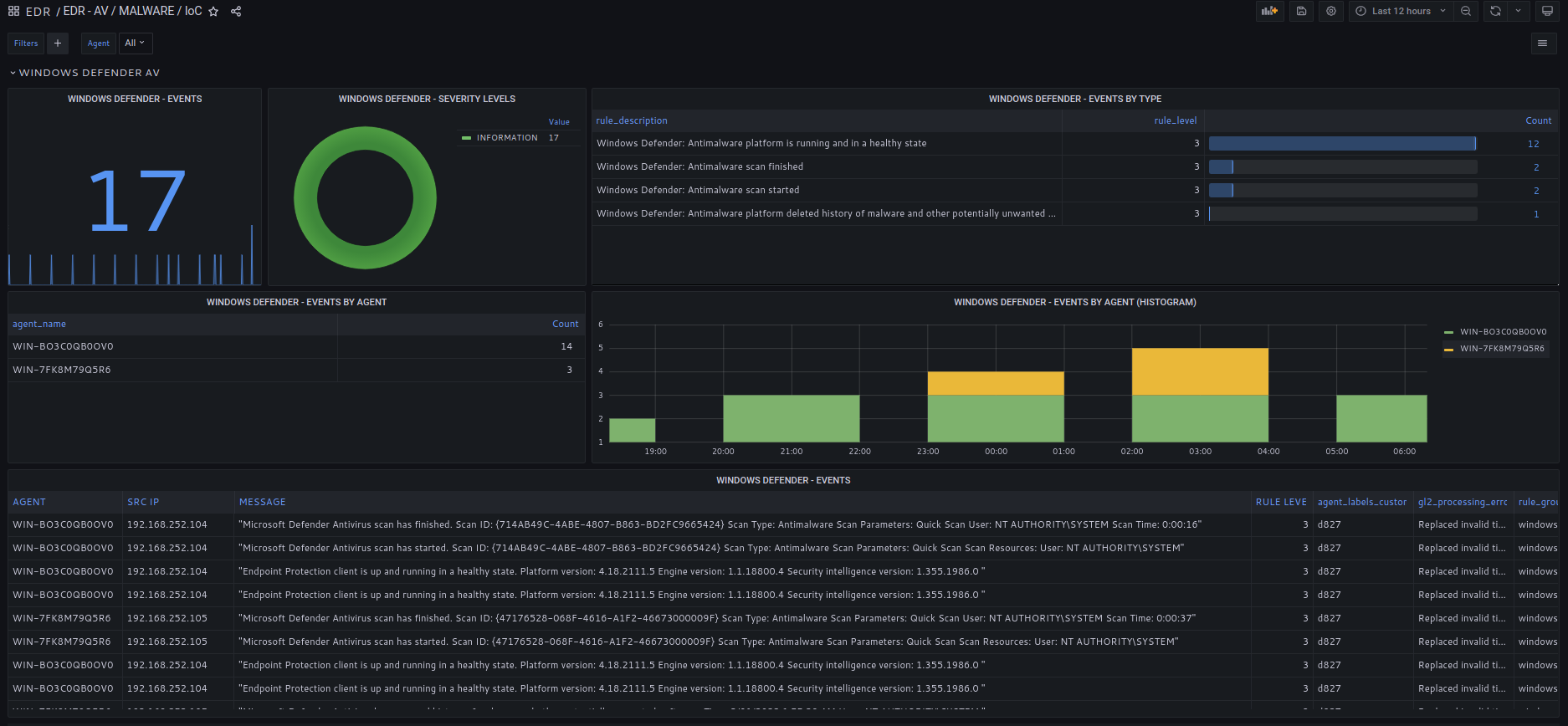
Windows Defender events are oftentimes overlooked or not properly collected and analyzed.
SOCFortress EDR collects and analyzes Windows Defender and Advanced Security events, including any attempt to disable the security tool.
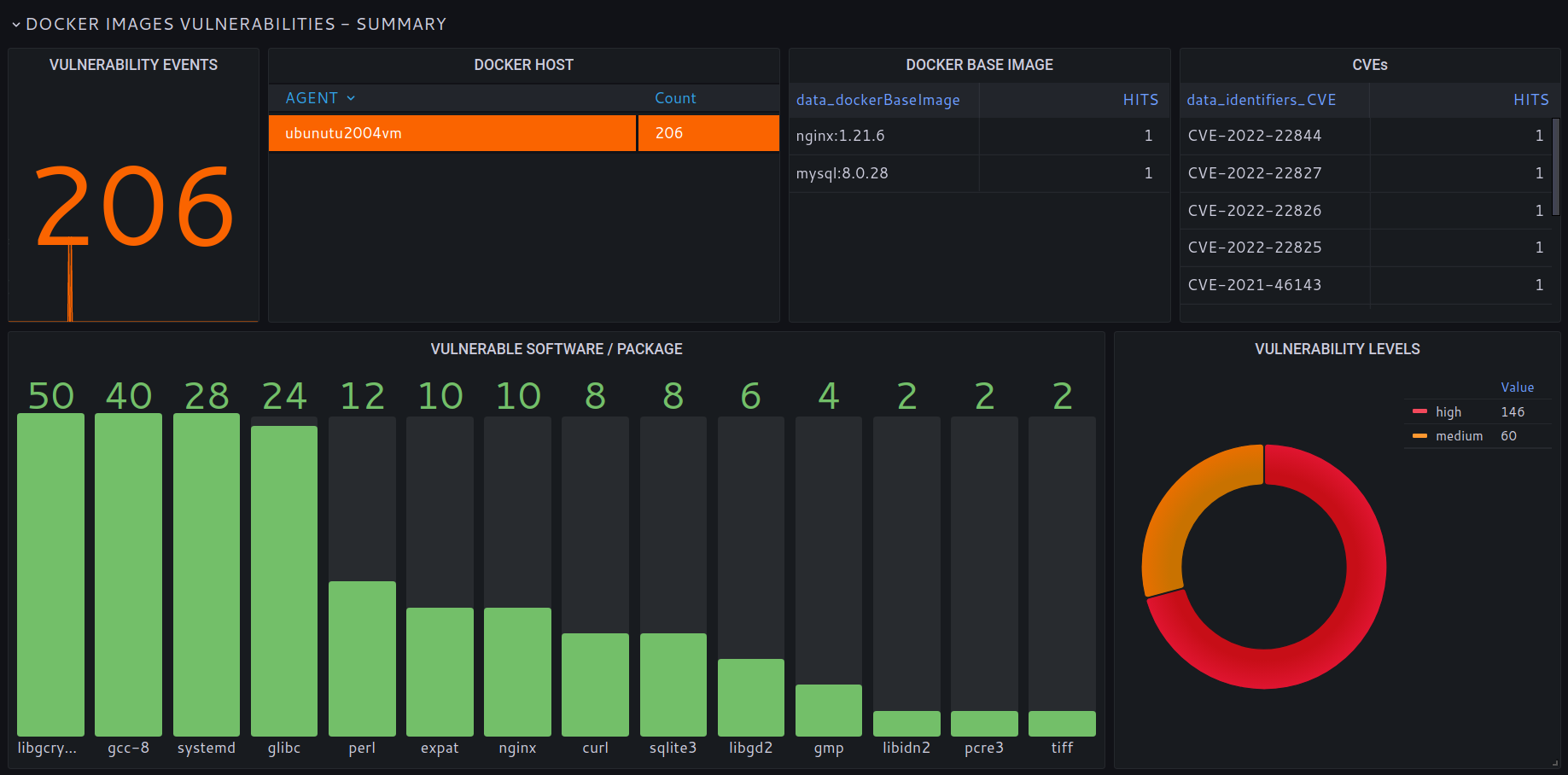
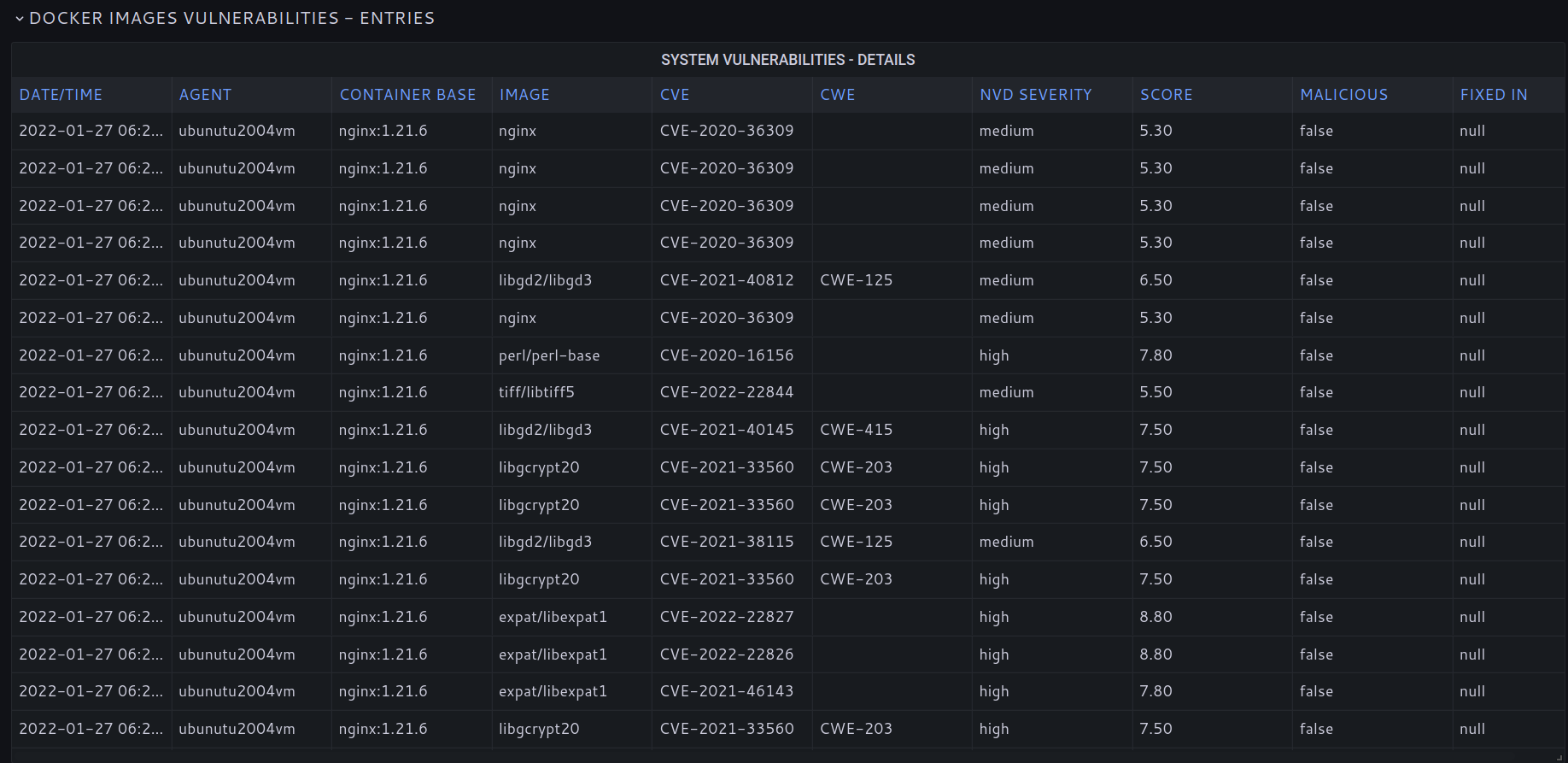
SOCFortress EDR agent inludes a vulnerability scan for Docker images. Aligned with NIST vulnerability database to find vulnerabilities in Docker images used to deploy containers. CVEs codes, description and scores included.
Keep all your containers and images up to date and avoid exploitation of well-known vulnerabilities.