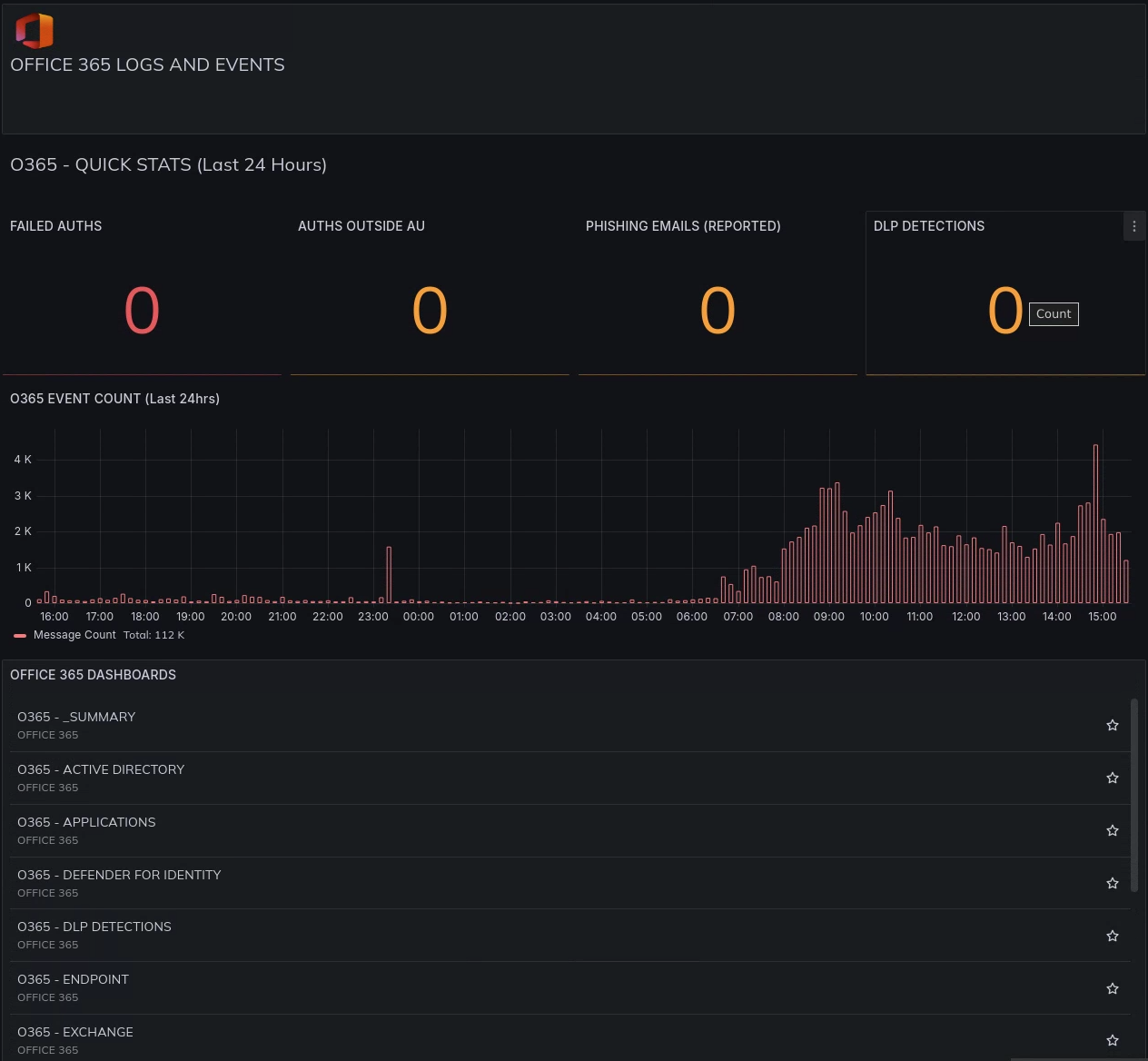
Azure AD User and Device events.
Office 365 events grouped by Workload and Operation.
Full visibilty on MS Defender for O365 alerts.
Exchange online and MS Threat Intel for phishing email detection.

Azure AD User and Device events.
Office 365 events grouped by Workload and Operation.
Full visibilty on MS Defender for O365 alerts.
Exchange online and MS Threat Intel for phishing email detection.
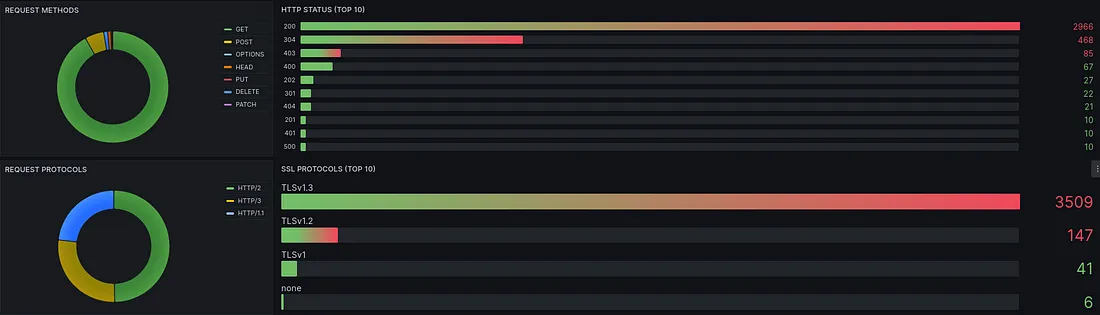
Cloudflare aims to make the internet safer, faster, and more reliable for users and website owners.
Content Delivery Network (CDN), DDoS Protection, DNS Management, SSL/TLS Encryption, Web Application Firewall (WAF), Load Balancing and Traffic Routing.
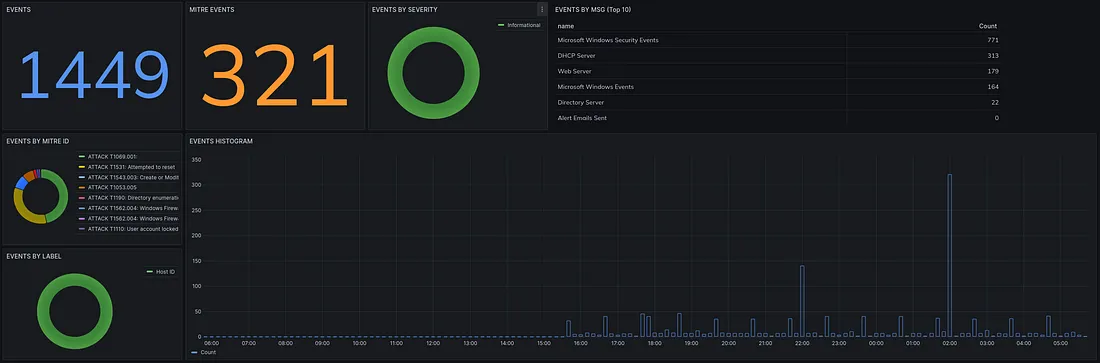
Deep Security is a comprehensive security platform designed to protect servers, virtual machines, containers, and cloud workloads across hybrid and multi-cloud environments.
Deep Security provides compliance scanning and reporting features to help organizations achieve and maintain compliance with industry regulations and security standards.
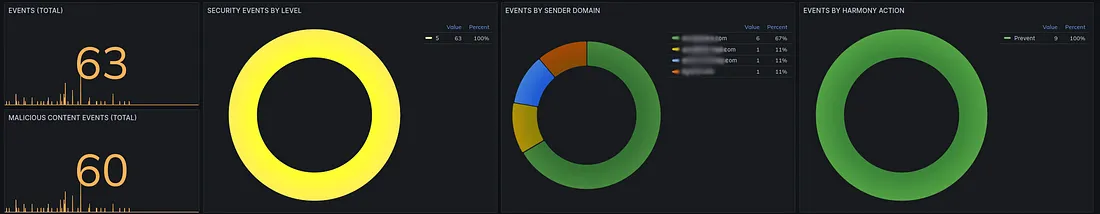
Comprehensive security platform designed to provide unified threat management (UTM) capabilities, combining various security features into a single, integrated solution.
The platform provides centralized security management capabilities, allowing administrators to configure, monitor, and manage security policies across the entire network from a single console.
Google Workspace, formerly known as G Suite, is a suite of cloud-based collaboration and productivity tools developed by Google.
Google Workspace provides security features such as two-factor authentication, encryption, and administrative controls for managing users, devices, and security settings.
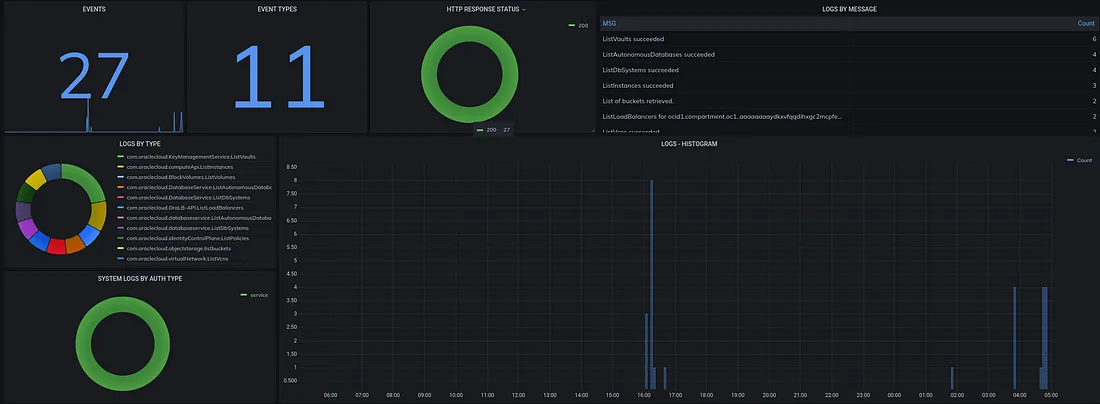
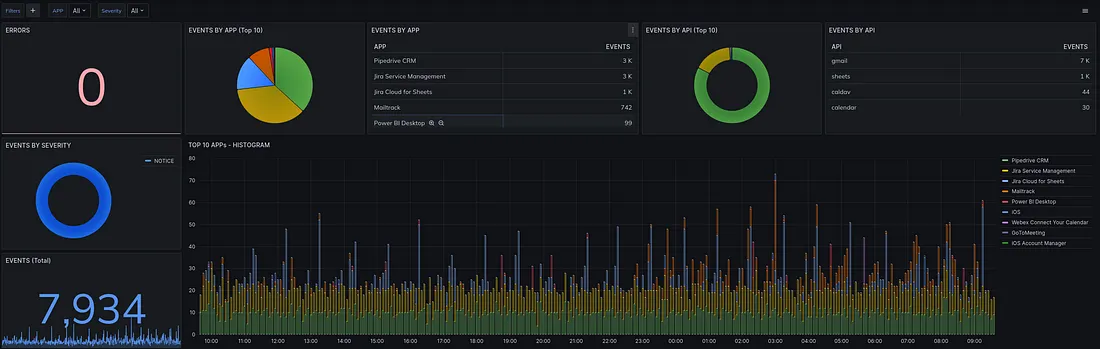
OCI offers a suite of cloud services that include computing, storage, networking, database, and various other infrastructure-related services.
Oracle Cloud Infrastructure (OCI) provides a comprehensive logging and monitoring framework that allows you to capture, analyze, and manage logs and events generated by your resources and services.
Logging Service (Logging), Audit Service (Audit), Event Service (Events).
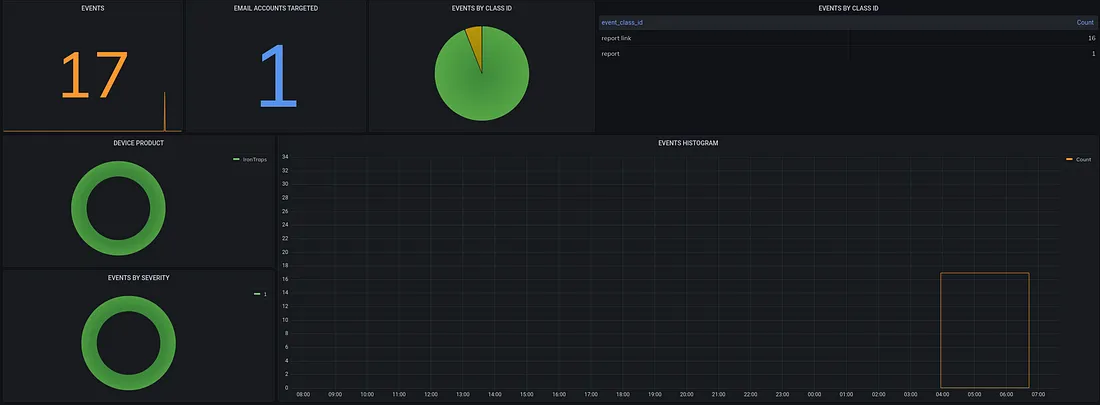
Ironscales provide solutions to protect organizations from phishing attacks, ransomware, and other email-based threats.
Phishing Detection, Real-Time Email Threat Response, Employee Training and Awareness, Threat Intelligence Sharing, Integration with Email Platforms.
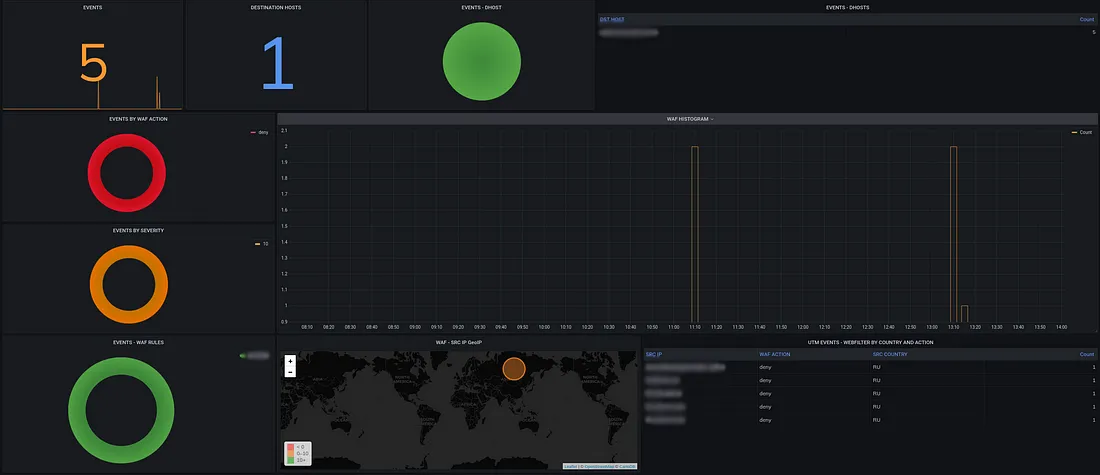
cloud-based security solution designed to protect web applications and websites from various online threats and cyberattacks.
Cloud-Based Protection, Security Policies, Threat Detection, Rate Limiting and Bot Management, Real-Time Updates, Monitoring and Reporting, Compliance and Regulatory Support.
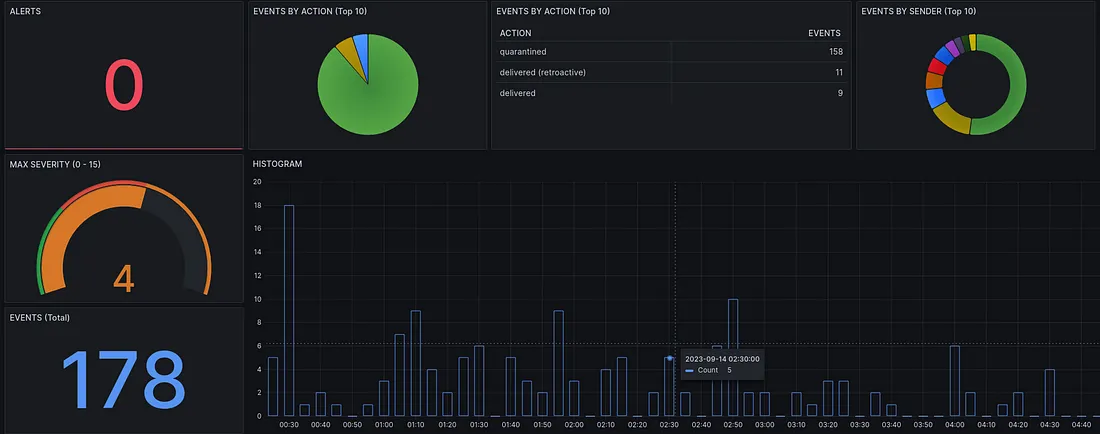
A Secure Email Gateway (SEG) that helps organizations minimize the risk of breaches by blocking inbound and outbound malware, phishing URLs, impersonation techniques, and spam.
Includes the ability to monitor email queues and advanced debugging options using email trace.
Threat detection, Enhanced AVAS protection, Executive impersonation protection, Supports custom YARA rules.
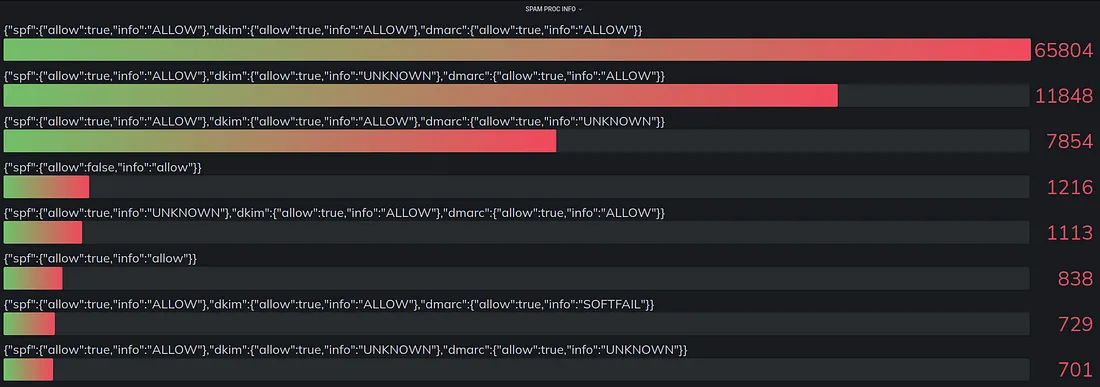
Helping businesses protect their email communications from various threats, ensure email continuity, and simplify email management.
Email Security, Phishing Protection, Data Loss Prevention (DLP), Threat Intelligence, User Awareness Training.
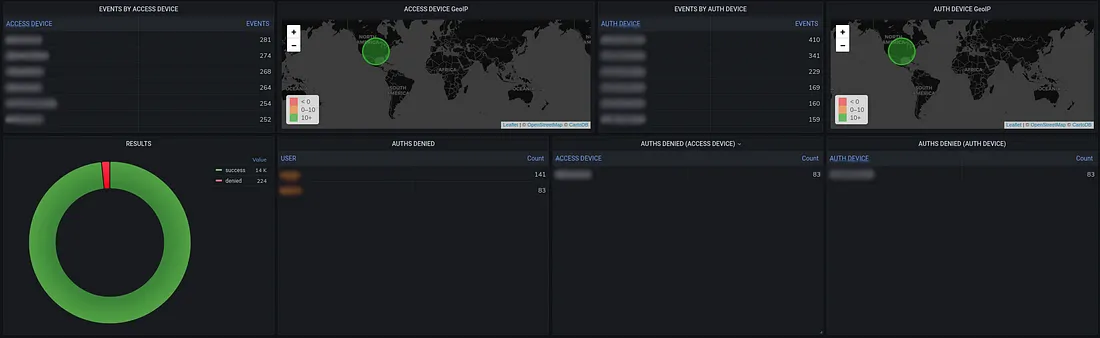
Duo Security’s solutions are widely used across industries to protect critical systems, applications, and data.
Duo Authentication offers a comprehensive MFA solution that helps organizations ensure secure access to their digital systems and applications.
Multi-Factor Authentication (MFA), Access Policies and Controls, Adaptive Authentication.
Azure Logs: User and Device Management.
User and Device provisioning.
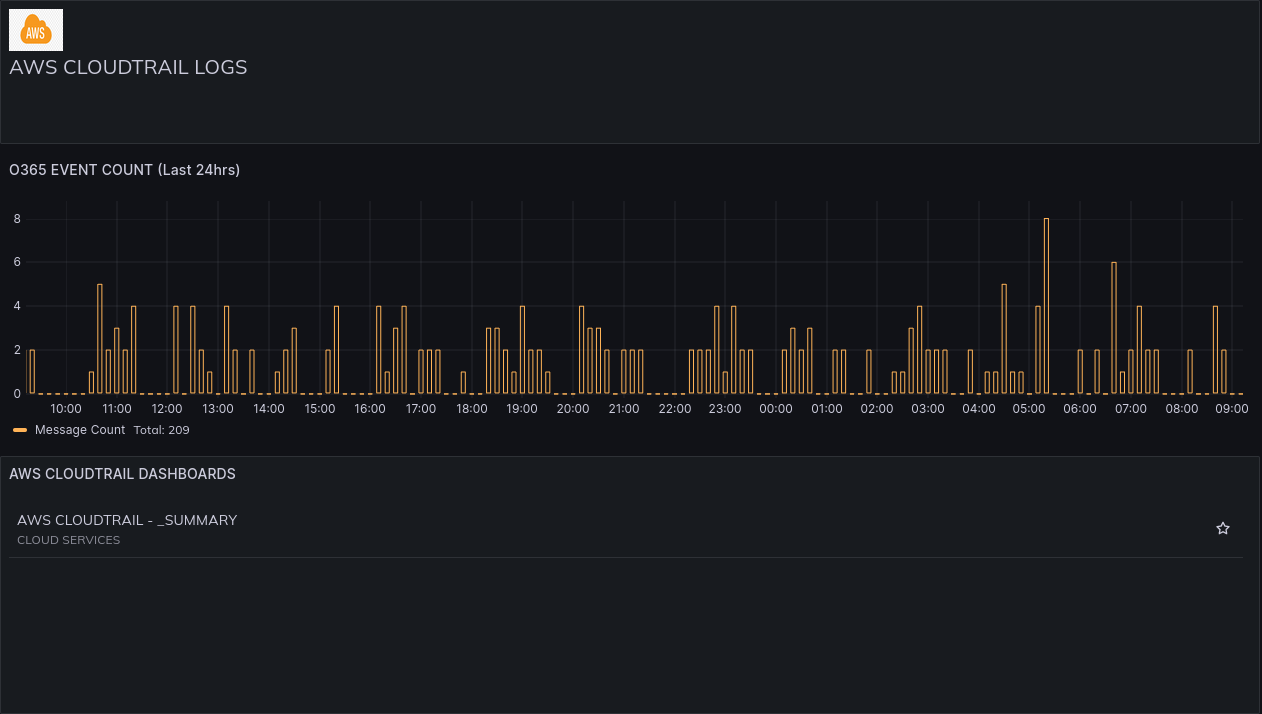
AWS CloudTrail.
Log AWS activity and events: ListGroups, CreateTags, DeleteSnapshot, CopySnapshot, AllocateAddress, AssociateAddress, etc.