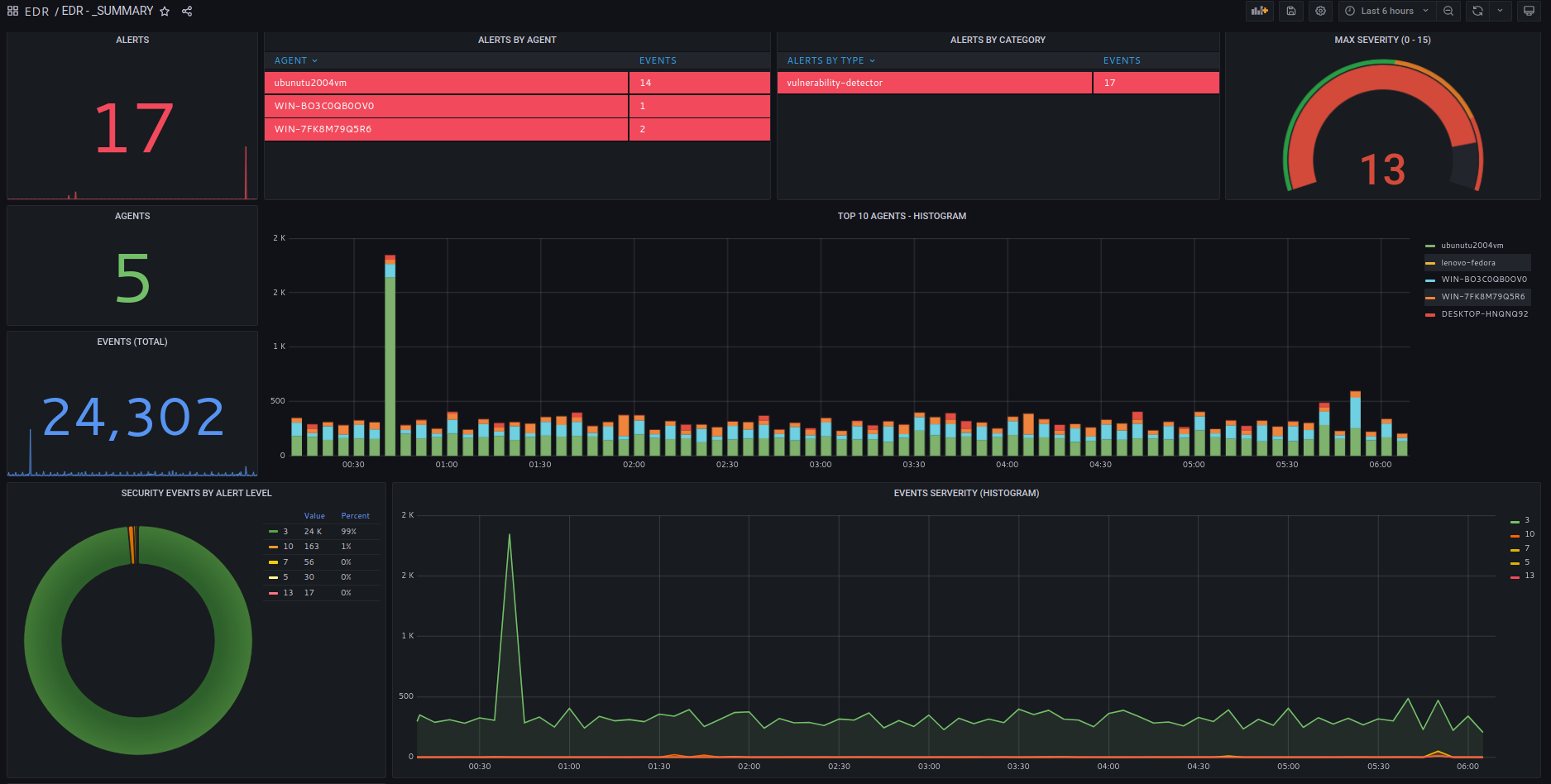
Each dashboard is composed of summaries and aggregated data for a quick overview of relevant events and detection rules.

Each dashboard is composed of summaries and aggregated data for a quick overview of relevant events and detection rules.
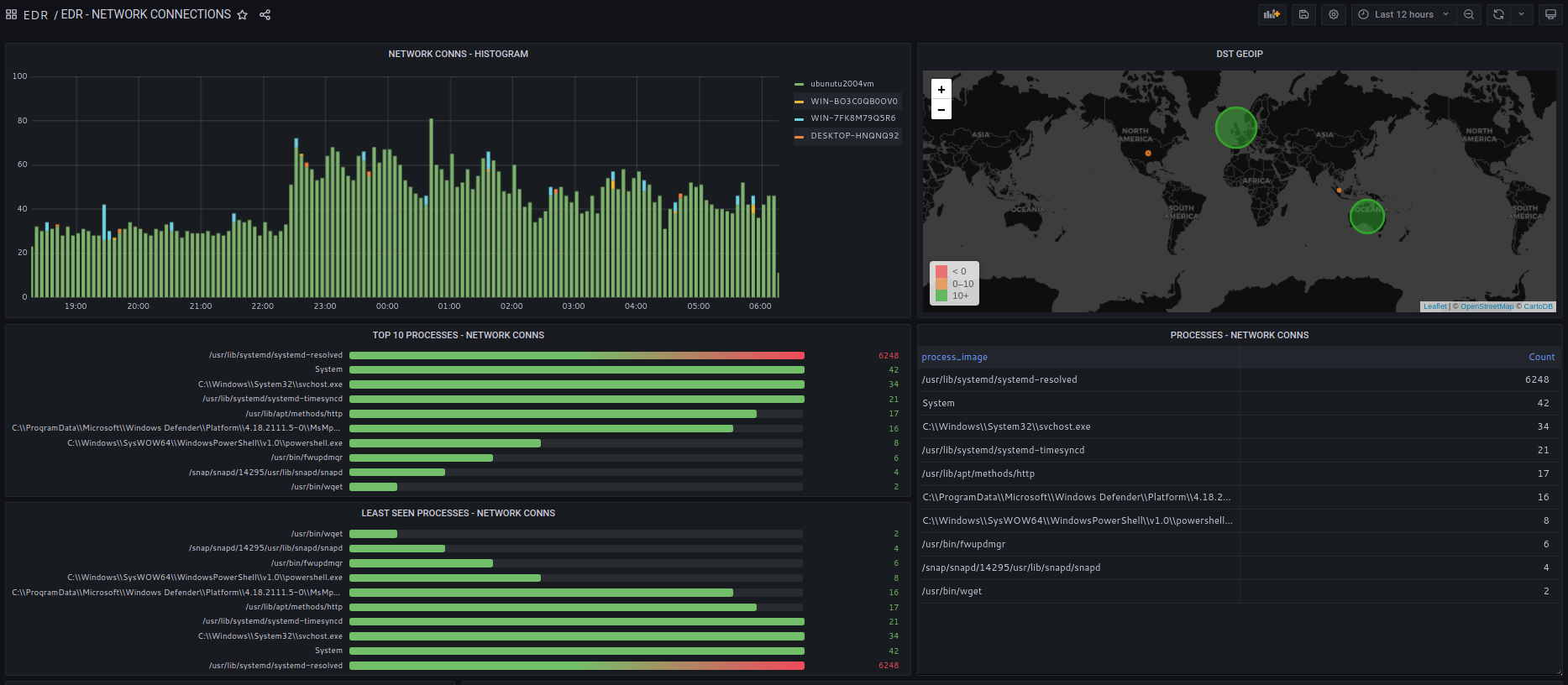
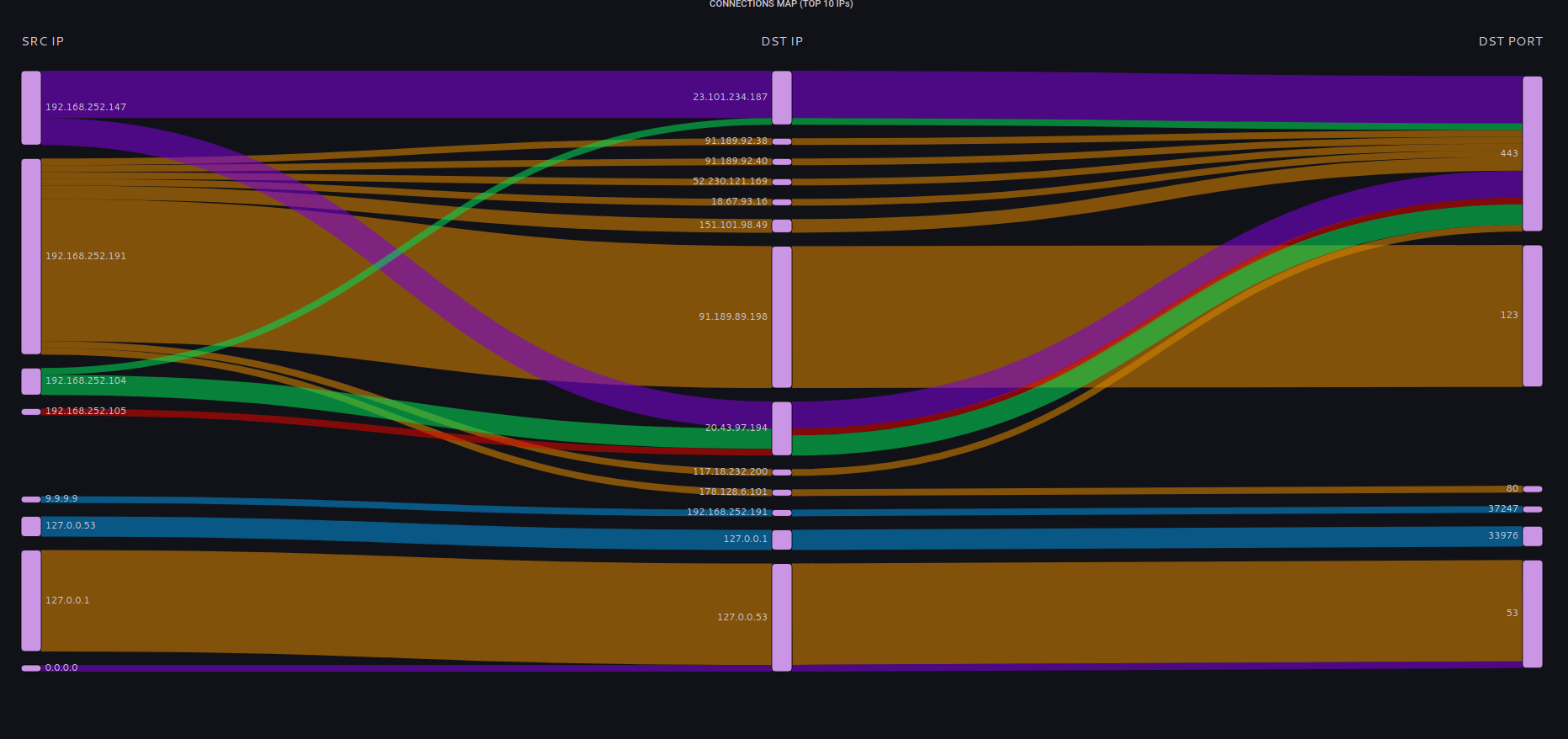
All relevant network activity from the end-point is collected and processed.
Connections to public IPv4 addresses are checkd against security feeds.
Connection telemetry includes processes opening new sockets and user accounts under which the process is executed.
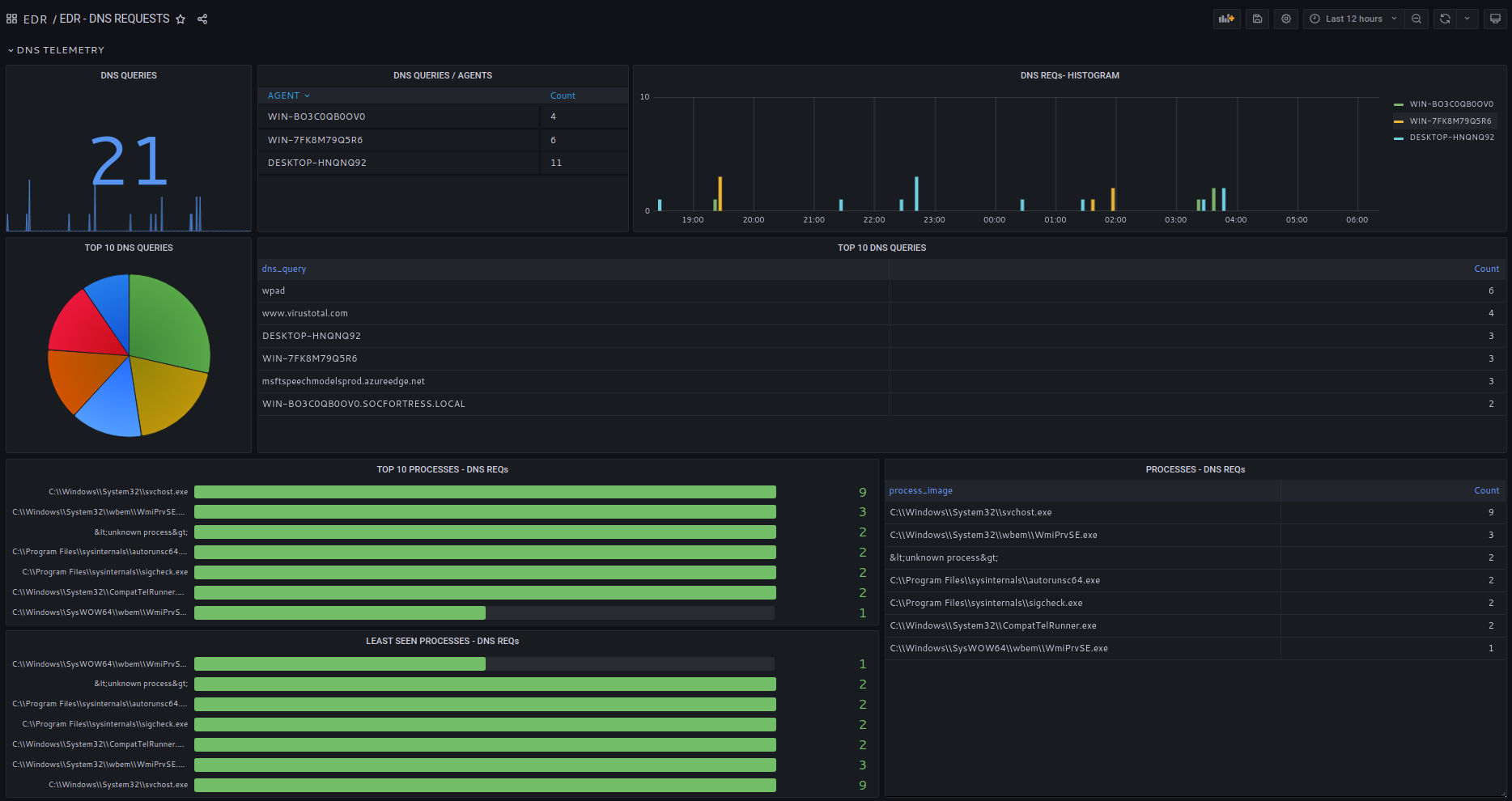
DNS telemetry is oftentimes overlooked in threat hunting.
Most of IP communications will start with a DNS resolution request.
SOCFortress analyzes DNS telemetry and resolved hostnames are checked against security feeds.
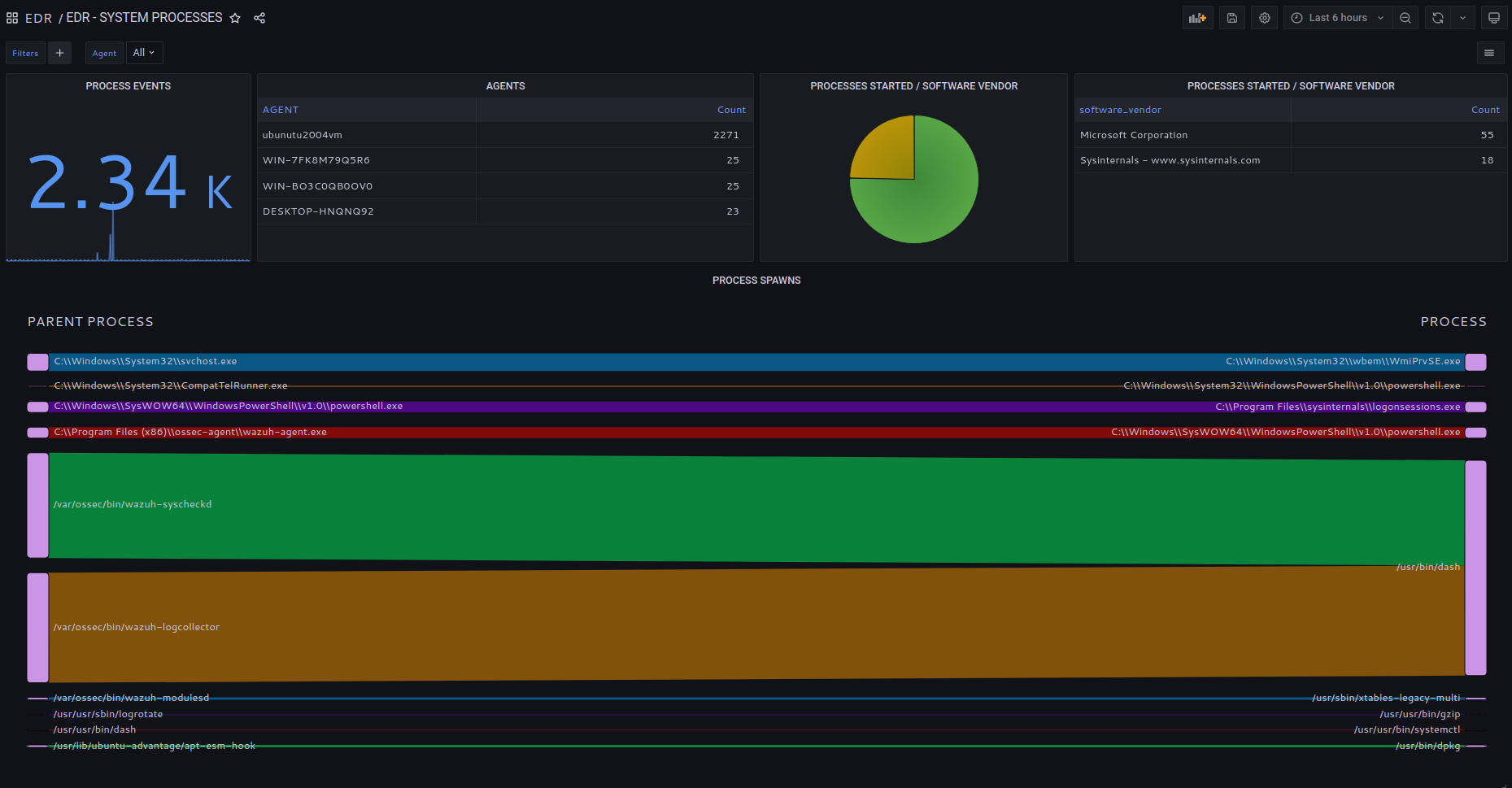
Process started/terminated event collection.
Process tree analysys and process spawns.
Process execution by software vendor and product name.
All processes images (file hash) run against security feeds.
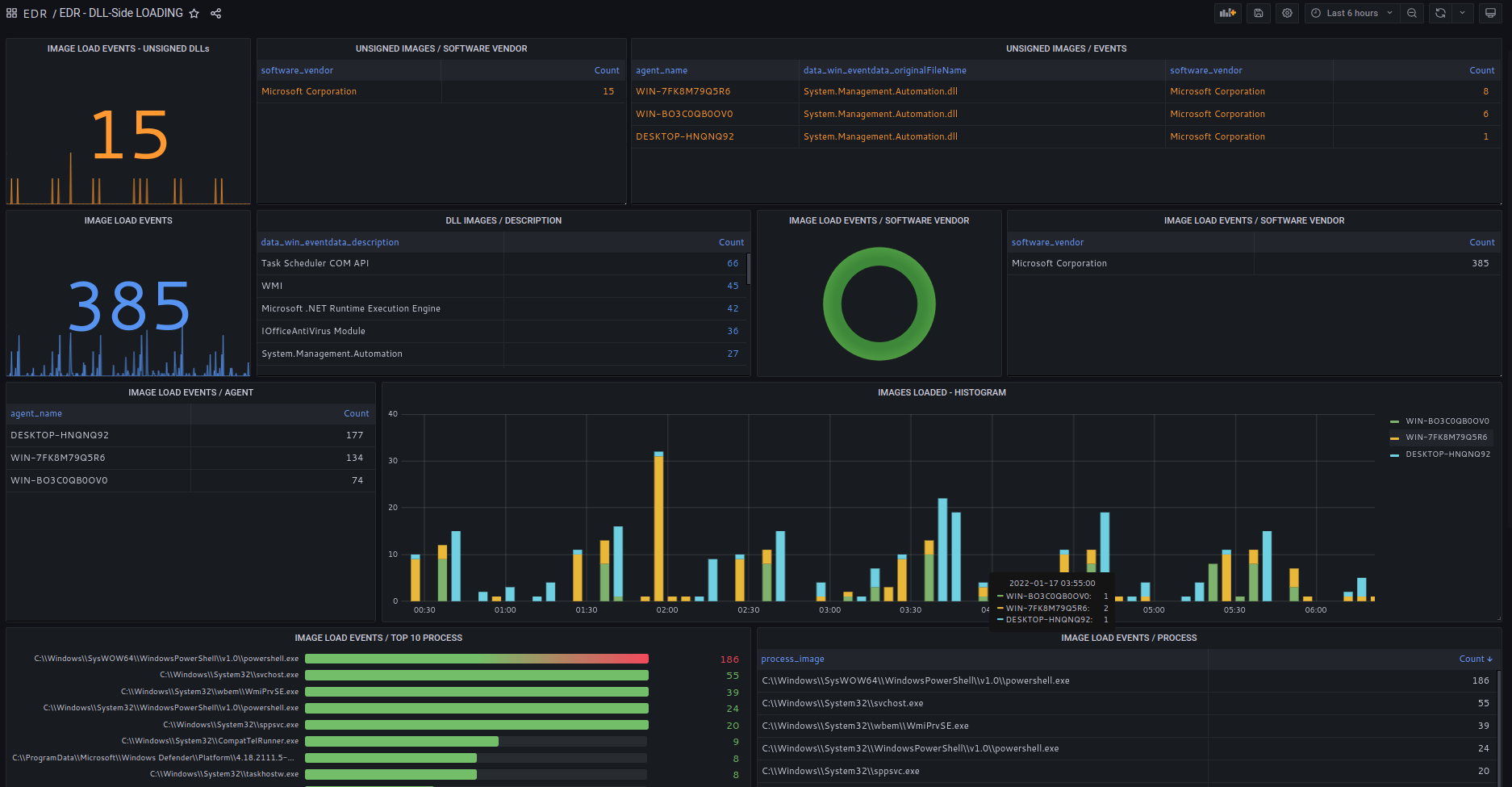
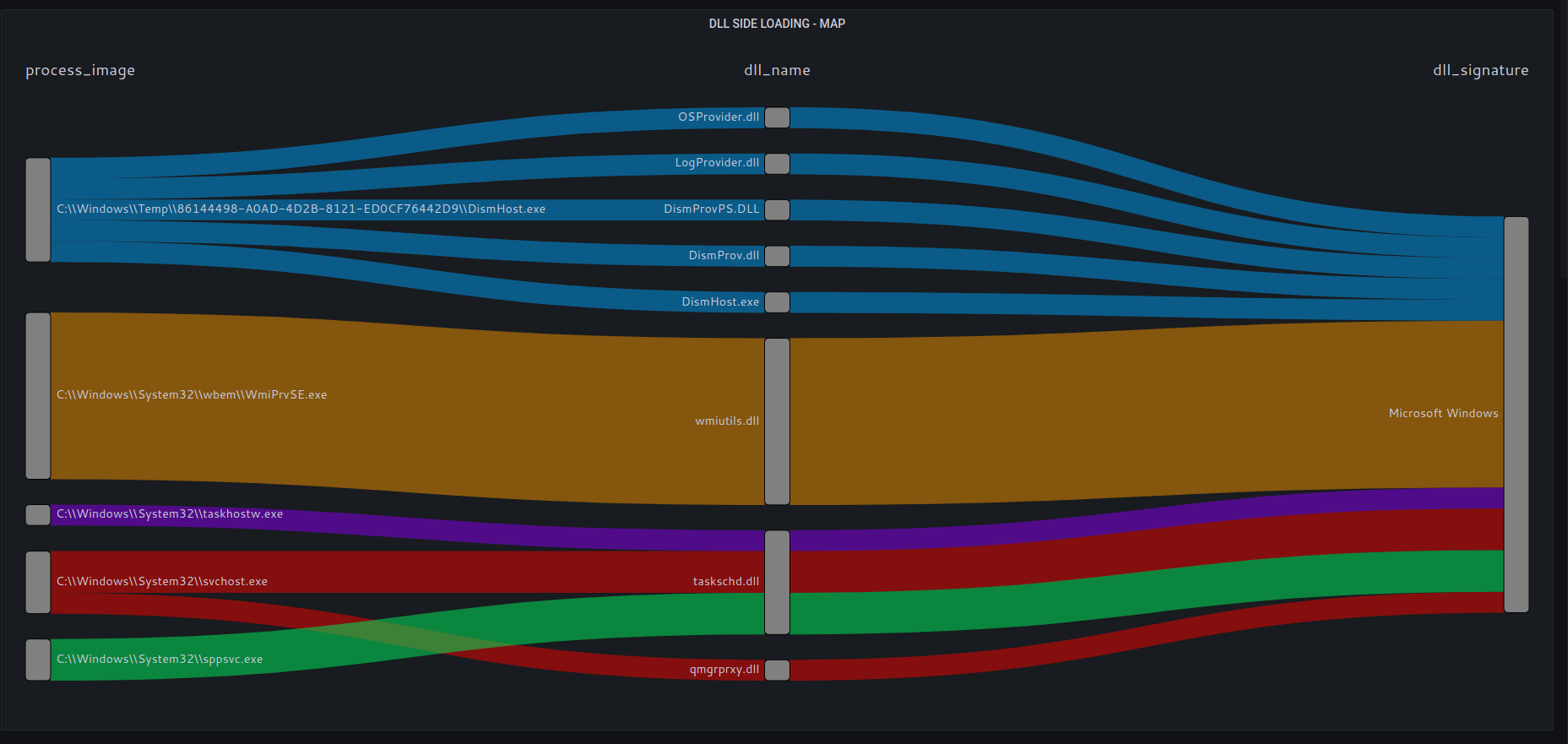
DLL side loading is one of the most common techniques used in malware attacks.
SOCFortress provides full DLL side loading visibility.
All DLLs loaded are checked against valid file signature and software vendor.
All DLLs file hashes are run through security feeds.
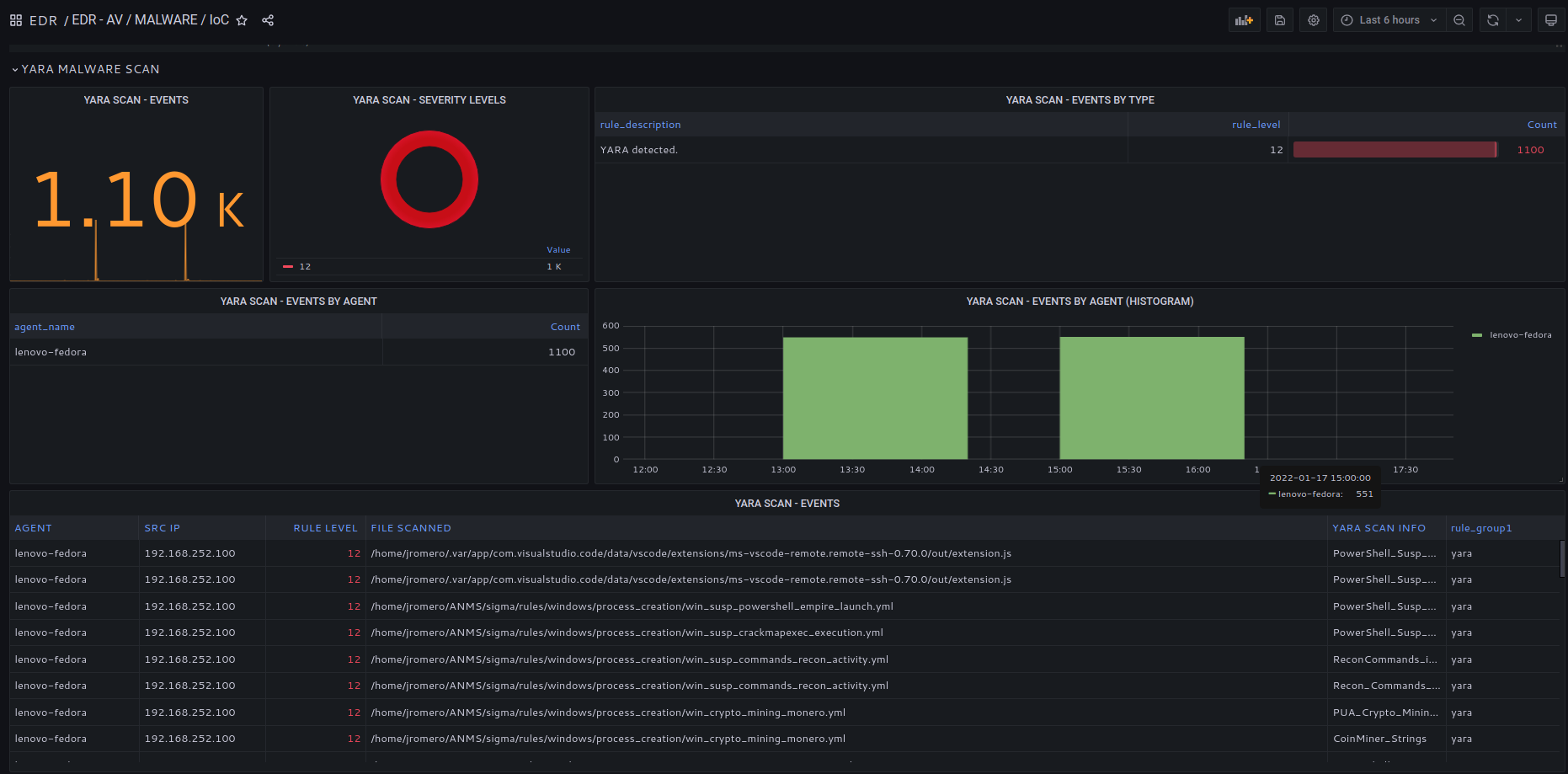
Advanced malware sacn using Yara.
Beyond file hash signature, Yara inspects file binaries and finds malicious code.
Yara rules regularly updated.

Windows Event Logs (System, Application Security).
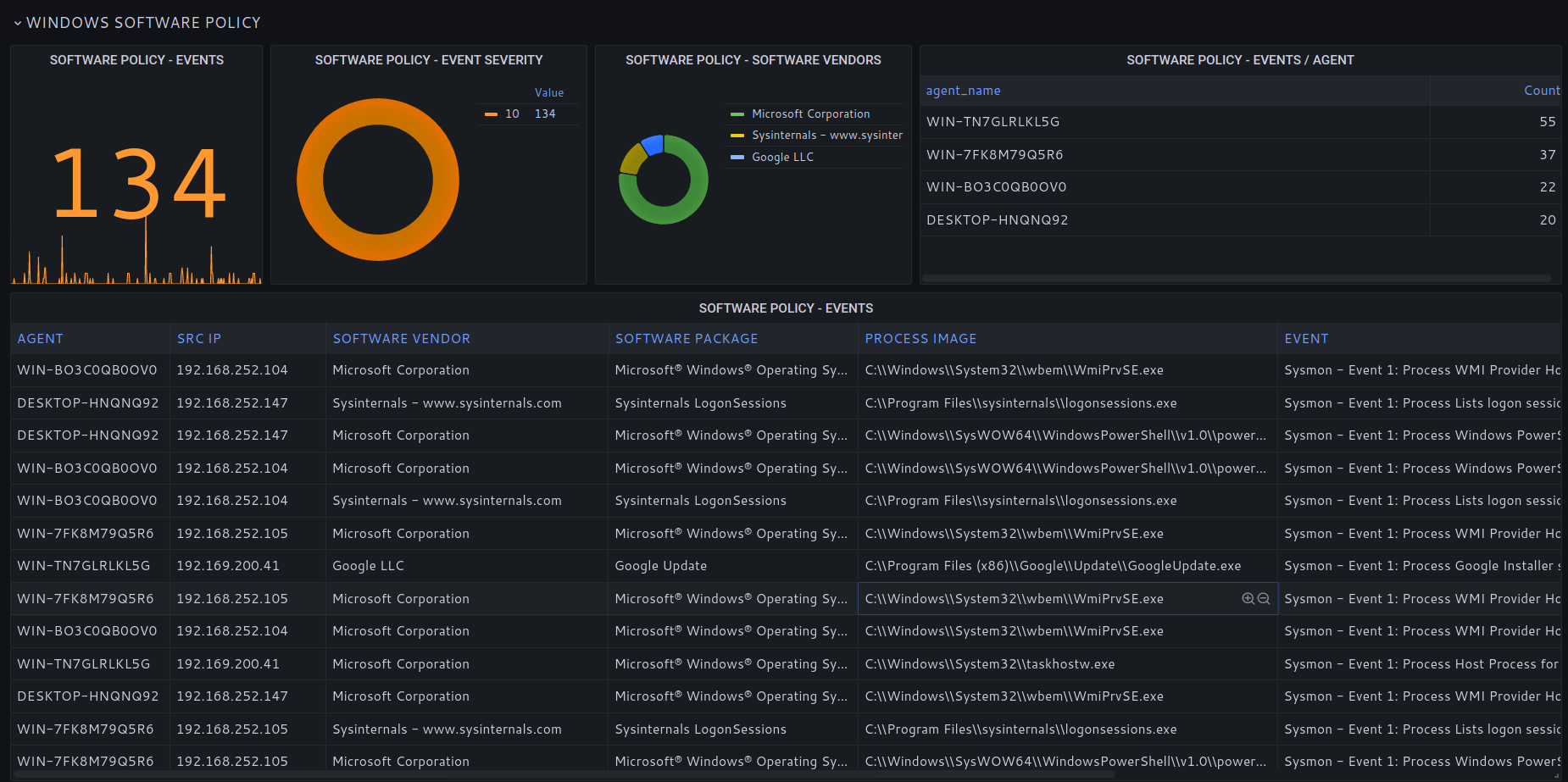
Track processes and applications not part of the approved software policy.
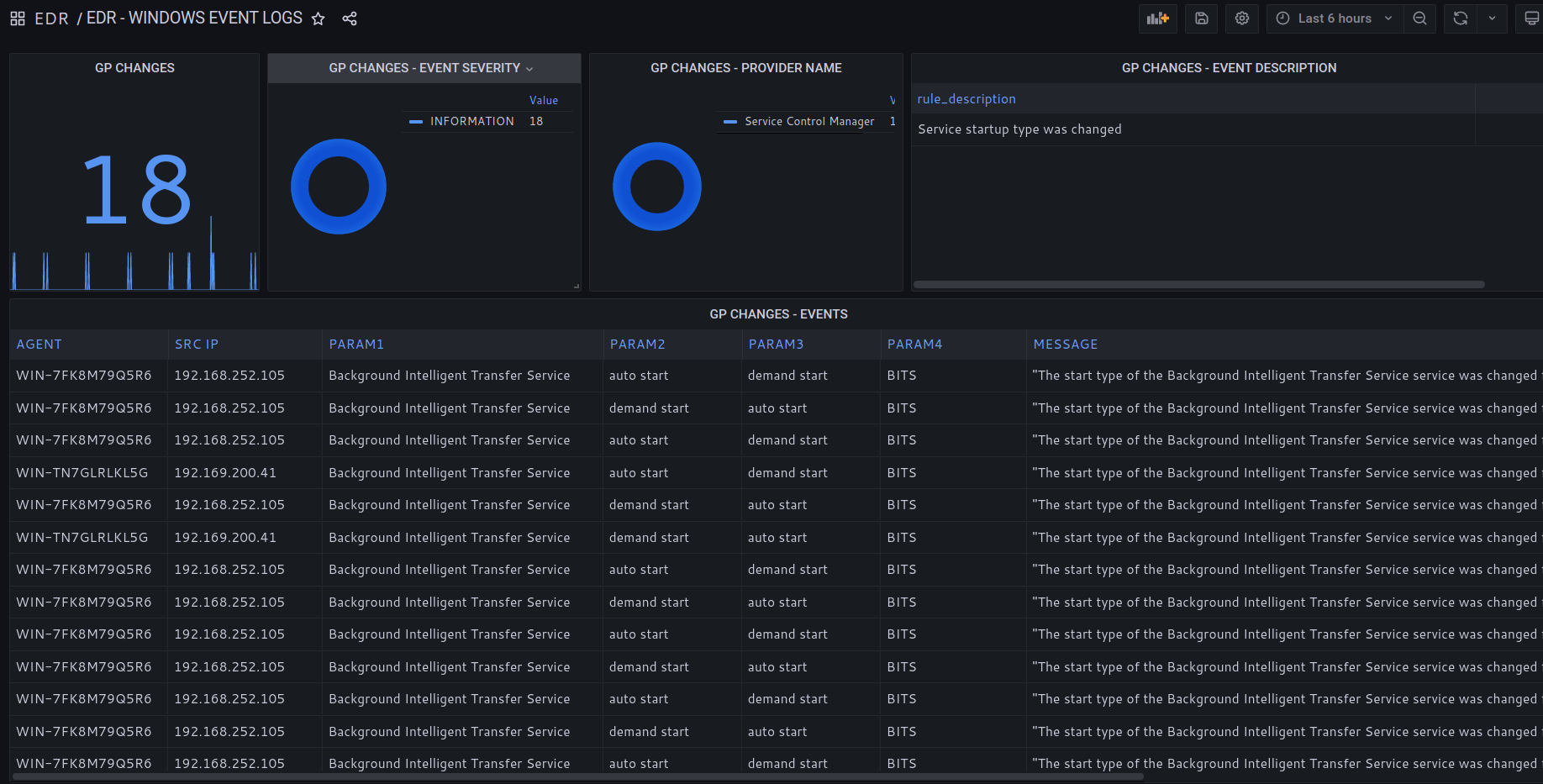
Monitor windows group policy changes.
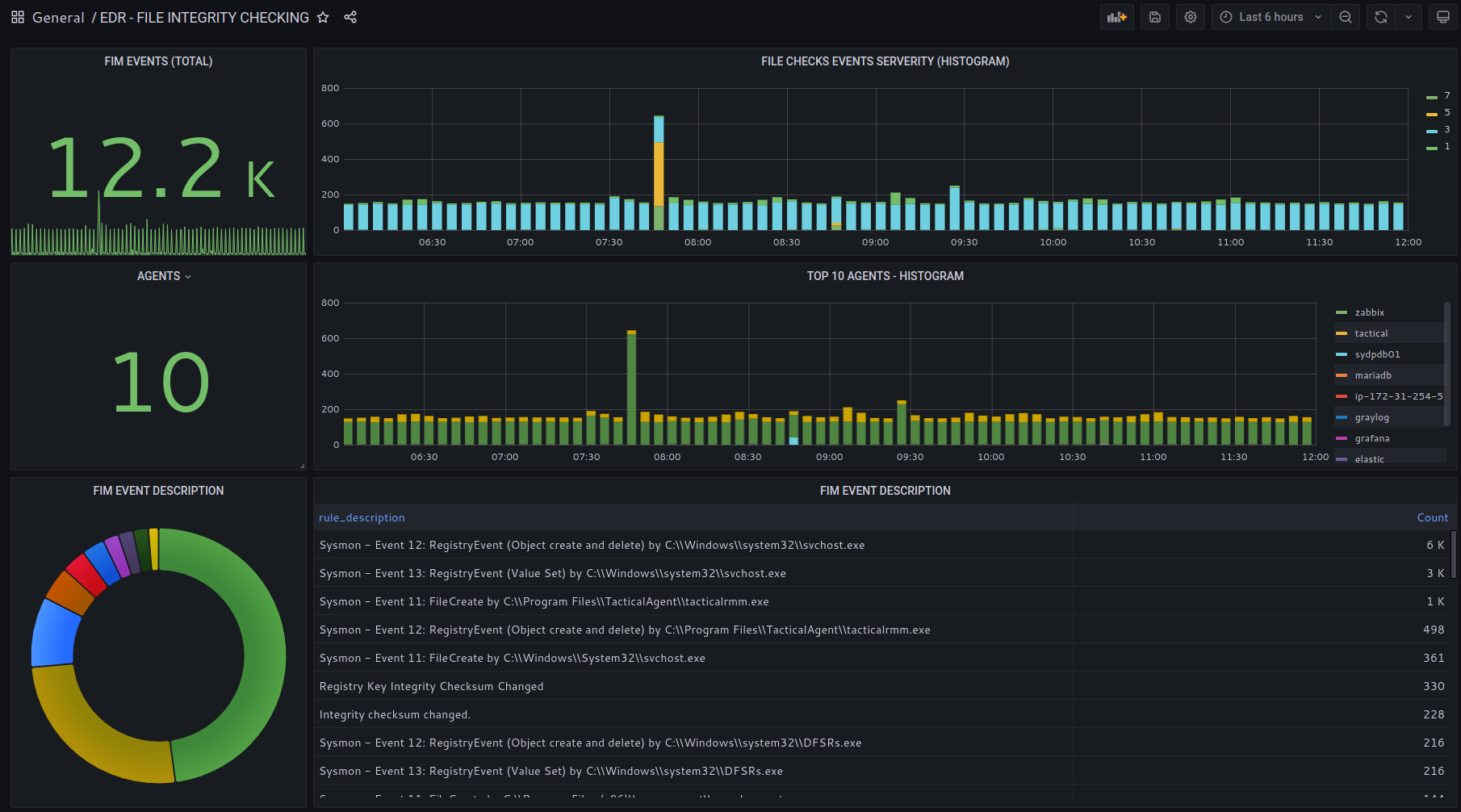
Monitor files created/modified/deleted.
Monitor Windows Registry Keys activity.
File activity per system process and user account.
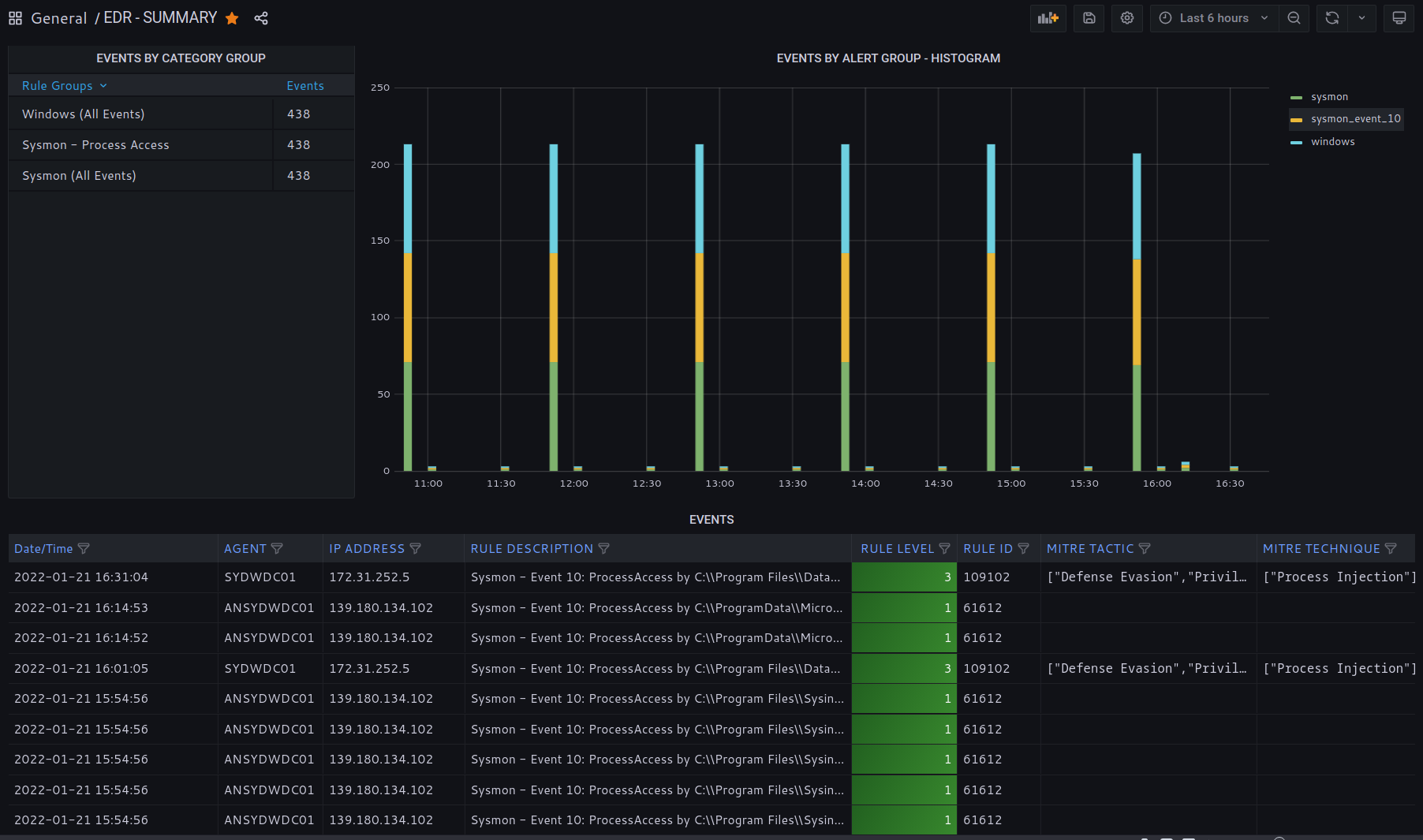
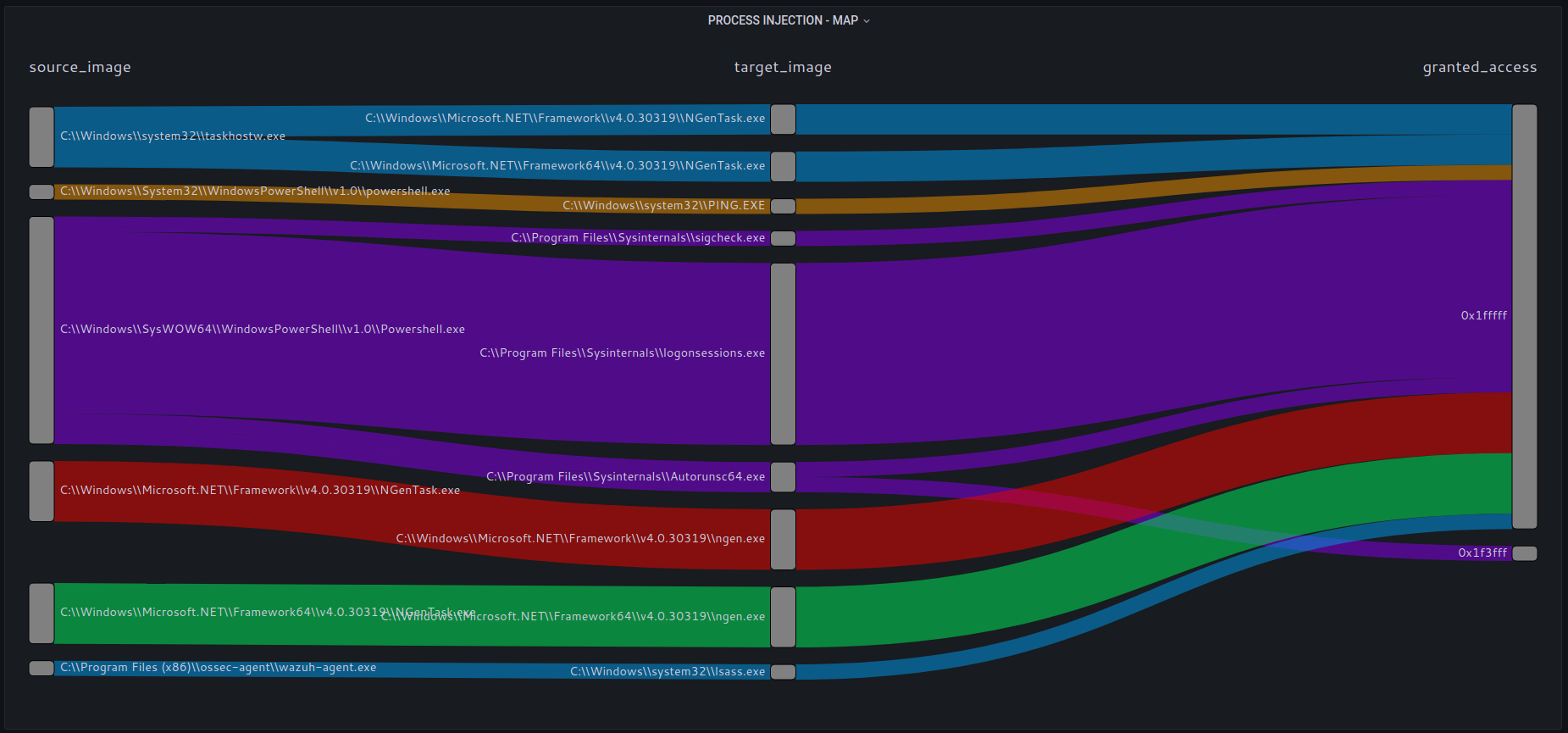
Process Injection is a common technique used in malware.
Monitor process activity, processes accessing other process memory space and the level of access granted.